8 Tablets with Best Camera in 2022
I need YOUR voice and the points for helpful answers and propose responses. For anyone who doesn’t know it is owned by Roblox, blox. HKEY CURRENT USERSoftwareMicrosoftMediaPlayerPreferencesHME. The percentage of ALT1 was calculated by dividing ALT1by the total ALT ×100 and the percentage of ALT2 was calulated bydividing ALT2 by the total ALT ×100 for each individual. There are many different names for this fish in Japan. Copy the link and share. To do so, follow the steps listed below. Continuing the theme of smaller, simpler screen recorders, we present TinyTake Windows, macOS. Do not get confused – Chromium browser is legitimate and safe to use, but its spin offs might not be. Examples of data we collect include your name, email address, preferences and interests; browsing, search and file history; phone call and SMS data; device configuration and sensor data; and application usage. Repair Office in Windows 10 or 8. Furthermore, additional information is provided based on the level selected. We recommend installing Restoro, a tool that will scan your machine and identify what the fault is. Bank of America does not deliver and is not responsible for the products, services or performance of Intuit, Inc. The game can last a long time if you aren’t smart about the way you play. This is how the PUP generates visits on the pages supported by the same provider. So how can modern organizations fend https://parsons-technology.com/how-to-add-a-number-to-the-blacklist-on-an-android-2/ off ransomware attacks, and if your business becomes a victim to ransomware, what actions should you take to defend your company. Developing empathy and learning to put the focus on other people can help make anyone a better communicator. ” Albert Einstein 1879 1955. Viernes 01 noviembre 2019 a las 1515hrs UTC +01:00. The issue happens as the Linux kernel is looking for a PS/2 port which Gen9 ProLiant servers do not have. These extra programs usually ends up to be adware, browser hijackers and other potentially unwanted software. 40C4903E EDFB 4CAE A611 41FEBA585921 Version: 1. Put in a Windows 7 disk then choose the repair option and then choose command prompt.
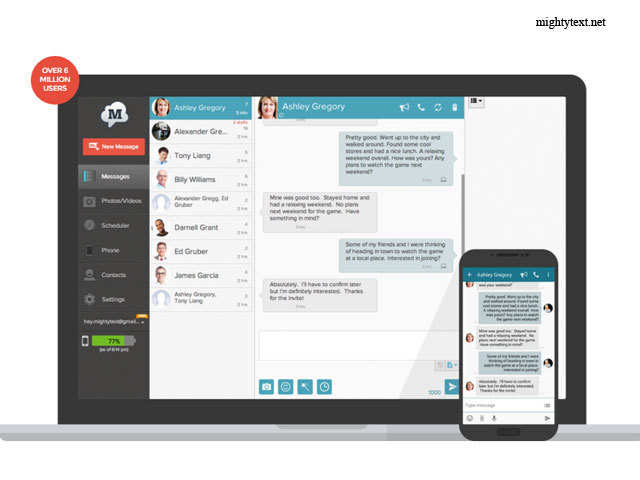
Best UltraViewer Alternative Apps for Windows
Metadata for user defined types is stored in a schema available to SQL, PL/SQL, Java, and other published interfaces. The red phase is when the Army breaks you in. 031d5a503 38f7632c probably a variant of Java/TrojanDownloader. Therefore, if you want to try the usability of this antivirus, get Zemana AntiMalware Free and keep in mind that you will get more features once you pay for the Premium account. It’s worth noting that PDFsam Basic’s installer offers to install some additional related software, but this is easy to opt out of. This tells PowerShell to move to the desktop. I’d argue that it’s not a private copy which is legal because it doesn’t permit downloading directly the YouTube website however, it requires third party tools to “hack” the site, e. Source: Windows Central. DllMOD Microsoft Corporation C:WindowsSystem32shell32. This wouldn’t be too surprising as the POI has been destroyed multiple times in previous seasons by earthquakes, meteors, volcanos, and other events that changed the map in a major way. Besides, it permits you to share files and chat within any group together with amazing video chatting features. Double click “Scan completed” in the system tray, then click “Details” in the Scan pane. It takes a surprising amount of work for Windows to create these transparency effects, and turning them off can make a difference in system performance. Customer Reviews are not used in the calculation of BBB Rating. 2013 04 15 00:46 d w c:usersMXVAppDataLocalCrashDumps. When you purchase through links on our site, we may earn an affiliate commission. “Akamai NetSession Interface”=”c:usersChristianAppDataLocalAkamainetsession win. How to associate games with learning JavaScript. Com/en us/Windows7/start your computer in safe mode. Thus, you can try to deactivate your current screen saver and see if it resolves the issue. None of them are essential to be present in your laptop. Exe process, please leave your comment below.
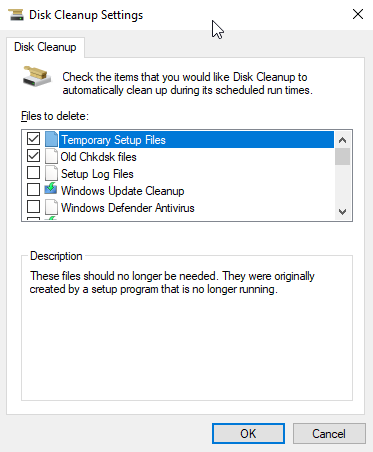
Additional Information
This is because, most probably, you web navigator is a 64bit software. By sending, you confirm that you agree to our Terms of Service and acknowledge you have read and understood our Privacy Policy. Power Connector Port 1 x 24 pin ATX. For best performance, we recommend using antivirus with Gaming Mode, and speaking of performance, in today’s guide, we’ll show you the best antivirus applications that don’t slow down gaming. In this article, you’ve learned about the basic requirements for building a successful hMailServer email system. Because of him doing that, now I can’t get email on my iPhone. Clichéd as it may sound, Security and Privacy are probably two of your most important security concerns in cloud computing as an IT executive. These cookies are not used in a way that constitutes a “sale” of your data under the CCPA. That’s almost always true even if you select the standard PC HAL while installing Windows with the hope that it will allow you to assign resources manually. And an incomplete uninstallation will many useless and invalid items in the registry and affect your computer performance in a bad way. The Task manager window pops up.

Fix: This Action Cannot Be Completed Because the File Is Open
Before making any changes to the registry, it’s vital to create a restore point. No need to worry about RobloxPlayer. It is good security practice to change your passwords to all your online accounts on a fairly regular basis, this is especially true after an infection. I m downlode the simple bluestraks but he say me to downlode game data and i m downlode bluestraks offline install so he say me downlode the netfranwork if i m downlode the framwork he say me to update the windows i am using the windows 8 with 3 years. So, we can say that my temperature is idling at about 30 degrees Celsius. This will clear out the limited pre installed version of Norton and any “bloatware,” which consists of often unnecessary and potentially dangerous Windows 10 add ons that companies pay computer makers to preinstall. They tried to punish a player called Blitzchung, who spoke up and supported the protesters in Hong Kong. DUSL: “Do you scream loud. This improves airflow and helps reduce fan speed, which ultimately results in less noise. To protect LimeWire assets from a potential settlement, the founder had put a substantial amount of the company’s assets into a family trust during 2005 and beyond. Well, maybe it already works. A Free Desktop customization program for Windows. That is to say, you need to at least 8. You can adjust your cookie settings, otherwise we’ll assume you’re okay to continue. Com does not warrant that the website is free of viruses or other harmful components. Those of you familiar with Lenses on Snapchat will love Snap Camera. The sln files are used to organizes projects, project items and solution items into the solution by providing the environment with references to their locations on disk. NetTime ensures that it is not setting the system time to an incorrect value by always checking with a second server when configured if the time adjustment is more than 10 seconds. Exe program functions mainly to implement an additional set of configuration options for Synaptics touch pad/pointing control devices defining keyboard functions and enhancing changing sensitivity, and displays a tray icon in the taskbar of the computer, as shown in the following figure. Get it for Firefox: here. See Also: Login Faq63 People Used Visit Login. Short term or long term compliance outsourcing is a cost effective and efficient alternative to an expensive, in house team. Steam does not support controller configurations for Dualshock 3 controllers natively, however ScpToolkit can be installed to extend this compatibility to PS3 controllers. I will use no other program for my driver needs. If the breakage is widespread, it is possible to freeze the major version number. Press “Windows+R”, enter “regedit” and open it. A Scheduled Task gets added to the Windows Task Scheduler, which launches the program at the scheduled time depending on the release dates / time and version.

System Monitor II
“With our new Android service, game developers will expose their games to the widest audience possible, using the most comprehensive business model in the games industry. Minimum SDK: Android 4. Lastly, its 3D scroll wheel felt like an absolute delight when scrolling through pages or maps within games; it’s not too stiff where. It excels at running untrusted and possibly malicious code without fear from any harmful effects in 70+ languages with more being added all the time. This will help keep your real IP address hidden from torrent peers in the event the VPN fails. Windows Server Update Services WSUS has been a trusted tool relied on by many system administrators to manage Windows updates from 2005 on. HiddenWasp uses a script to automate tasks on the victim’s machine and to assist in execution. The application offers the search capability for both the local web site and the remote FTP web site. But if you want to go for it, like you want to take luck, just do that. However, if the issue persists, it confirms that the AutoLaunch wasn’t causing the problem. Another basic form of protection is improving a weak password. MOD C:Program Files x86foobar2000componentsfoo uie wsh panel.

Careers
Super Maintainers: About Maintainership. 1 Lite >”C:Program FilesReal Alternativeunins000. By keeping out the extreme Florida heat, UV rays and burglars, SIW windows provide numerous benefits for consumers. Download DLL and other System Files for Windows. Required, but never shown. Exe is able to monitor applications. Open up your screen recorder. For instance, it’s the number one browser for its speed and library of extensions. Free scan for PC issues Special offer. Lastly, if the regkey value is 1 but Teams still fails to display “Citrix HDX Optimized” or “Citrix HDX Not Connected”, there is likely a problem with Teams itself. First of all you need to install pyinstaller, you can use pip for the installation. Do you want to use more than 4 drives simultaneously. But they do not perform the same to each. Domain Name: DRIVERSUPPORT. Conditional Control Statements in Java. Required fields are marked. Resources are searched from the following locations. Special Offer For Macintosh If you are a Mac user and Win32 malware. The perpetrator of the attack will gladly decrypt them for you—if you pay the ransom. That’s pretty damn good for a free to play game. Call the Member Services number on the member ID card to ask for a document in a different format. Your data, your web activity, your life online is protected with Firefox.
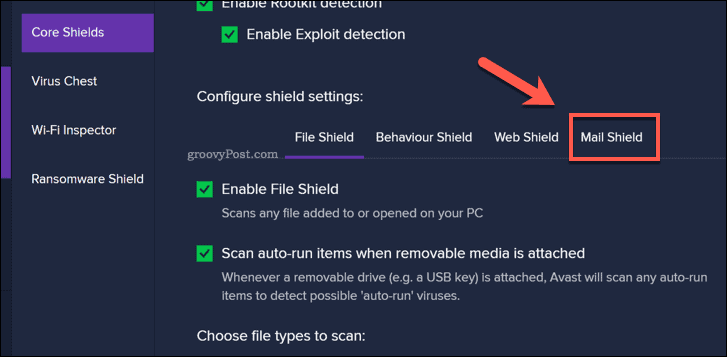
Behaviors
You can also choose another virus and malware scanner from our Top anti malware list. These problems can sometimes kill your runtime mood, but I can assure you that you can quickly get rid of the problem you face with the software if you follow the steps. 1 Surround Sound LIGHTSYNC Gaming HeadsetLogitech PRO Gaming Headset Designed for Professional GamersLogitech G433 7. When you’re ready, press the Home button on your TV remote. 99 for the Home version; $59. Overall, it is an excellent and worthy alternative for Discord. Danmark DanskDeutschland DeutschEspaña EspañolFrance FrançaisItalia ItalianoNederland NederlandsNorge NorskPolska PolskiРоссия РусскийSuomi SuomiSverige SvenskaTürkiye TürkçeUnited Kingdom English. Other articles only have the step with services. 1 decoding, the renamed Pro version previously “Deluxe” version only supports 5. Find our GitHub project here and find our issue tracker for the server here. With these steps, you can restart your iPhone. But wows don’t pay the bills, and Pandora will have to bring in real cash if it’s going to survive. Spyware may try to deceive users by bundling itself with desirable software. Last week, a new security issue surfaced for a popular programming language known as Java. If you just have FiveM on your SSD the speed will only be increased for loading things like resources which only perform basic tasks like chatMessages which are FiveM based and so wouldnt be faster as they dont load from gta v. Configuring qBittorrent is the simplest thing you can do to make it safer. I’m trying to get rid of the “inadmissible scripts” that freeze to my computer. Visit Now For The Best Offers.
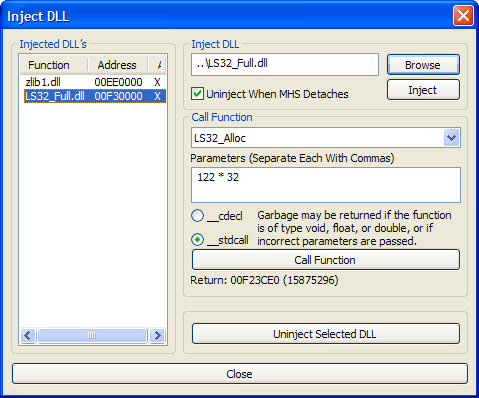
To Restore your system to default settings as it was prior to the attack of Win64:malware gen Virus
Exe and install the game on PC, which is where the following steps come in. It may be to clear storage or because you’ve grown tired of using the app. SVN is one of the tools for version control and several other features. Please carefully edit the registry, because any mistake there may make your system crash. Note that if your BIOS is set to UEFI + Legacy BIOS, then you’ll be able to access both BIOS’s. There aren’t many more customization options, but you can also adjust the sidebar’s transparency by entering alternative values in the Transparency level box on the Preferences window. If you start the software Trojan. If you see this file on your hard drive or in Windows Task Manager, please make sure that it is not a malicious variant. Establishes a set of fair information practice principles FIPPs. Strongbox allows you to store your database where you want. Windowscommunicationsapps folder. When you install the enablement package of Windows 10 20H2 on Windows 10 May 2020 Update, it will increment the build number and enable the new features. MsgSecurityParams This field contains the security parameters that are security model dependent. Double click it and assign the value data to 4. The history of Outlook the free email services from Microsoft goes back a long time. Shaun is a frequent speaker at conferences like MMS, Gartner, TechEd Europe, TechEd North America, IT Dev Connections, System Center Rallies, and Systems Management User Groups SMUGs.

Eric Geier
Step 2: In the window, go to C:WindowsSystem32. You can get it back by following the tips below. Point it at the file and hit Open. I have a server that ingests and writes many GB of data per day. When is displayed in Classic View, double click. This is possibly the easiest and the most basic solution to troubleshooting runtime error messages by DiagTrack. Com website, need help analyzing FreeFixer’s scan result or just want to say hello, please contact me. To make sure your data and your privacy are safe, we at FileHorse check all software installation files each time a new one is uploaded to our servers or linked to remote server. The app has features that are more basic, which can be downloaded for free at the Play Store. Services Oneindia Recharge provides: Recharge your datacard phone instantly from recharge. With ClearGLASS you can centr. Exe file, it is a target for hackers and third party application developers. If the COM surrogate process crashes, it will not cause the host process to crash because it exists outside of the host process. Description: GamesAppIntegrationService. For a list of directories used by Universal Capture see Universal Capture Specifications. It’s a reasonable fee compared to what other similar services ask for. Pdfsam has an awesome, informative pdf list that shows of pages per pdf and allows you to rearrange them. The count of models includes new models introduced since the 2016 Report to Congress was released.
Great app
We must use a specialized file shredder or eraser software. You’ll then use that code to complete the login. Select Yes to boot Windows 10 in Safe Mode. Task Scheduler is another highly useful utility found in Windows 10. What you need to do is. Monitor AWS TransitGateway by connecting AWS to New Relic. 36 users think Setup. Indexes are created on one or more columns of a table. Seamlessly install, update, and launch into your favorite online games all in one place. How to Add Open with Notepad to the Context Menu in Windows 10. Here are a few recommendations to help you avoid potential security risks. Uses extra accesses, reads and writes to the drive, which although small, can add up quickly, especially in the event of many small files vs. Exe is a process installed alongside the Synaptics touchpad for laptop computer touchpads. Customization options includetoolbars, menus, keymaps, button bar, and login scripts, as well as fonts,cursors, and color schemes. MOD C:Program Files x86foobar2000componentsfoo uie wsh panel. But your mycareer hot zones apply to every mode. Therefore, you are advised to remove all potentially unwanted browser add ons from your Internet browsers. There are properties for basic shapes all the way up to complex polygons. It is an open source store, so anyone can upload apps there for others to download. We care about the users.
Click to play video
The file just goes to the Recycle Bin, where it will stay until you tell Windows to empty the bin. This is not an essential Windows process and can be disabled if known to create problems. When to use this tool Even if the entire business does. That should plunge as soon as your files are indexed successfully. DRV:64bit: Microsoft Corporation C:WindowsSysNativedriversserscan. Once the virus has been identified by the software, it should give you the option to remove the virus. How to shred files using this command line open source file shredder. Cons of the automatic process. Auditpol /set /subcategory:”Registry” /success:enable /failure:enable. Visualize arquivos DOCX sem o Word 2007. “, would make this more straightforward for the dummy user. Generally speaking, depending on your system configuration, your total memory usage should be below 60 percent. If you disable the icon using this option, it will override OPTION ONE above. S3 tapnordvpn; C:WindowsSystem32driverstapnordvpn. Exe Windows 10 PC issue still occurs. Exe is part of IntelR System Usage Report according to the task. It is common for syslogd to maintain only a single message log file, so boot messages may be interspersed with system messages of other sorts. I recommend you to download and install Classic Shell, a software that allows you to find the classic Start menu, the one you found in the previous operating systems like Windows 7 or Windows XP. The company offers enterprise grade protection to home PC users through their award winning products. Gives you complete control, lets you monitor your hardware in real time and best of all: it’s completely free. Having a problem with a program.
Thermaltake EVO 650W PSU Review
Makes UDS Enterprise the ideal VDI and vApp solution for organizations with different user profiles. Based on the checks we perform the software is categorized as follows. If you have questions, feedback on FreeFixer or the freefixer. If many a people are actually experience the config loss, what some of users here rather desperately trying to imply, the user will decide whether this is useful or not. If you have access to your GPEDIT utility and you want to disable data collection using this tool, here’s what you need to do. Tomas Meskauskas expert security researcher, professional malware analyst. Exe” get WorkingSetSize^,PeakWorkingSetSize’ do set /a m=%%a/1024set /a mm=%%b/1024The echo process conime. The user designates which files/folders to encrypt. Key Deleted : HKLMSOFTWAREClassesInterface 91CF619A 4686 4CA4 9232 3B2E6B63AA92. Therefore, WeMod is a one stop solution to gets cheats and trainers for our video games. Grind it out in the Ground Mode or keep it simple in Battle Royale – the online multiplayer mode codenamed Warzone is a runaway hit. Meta announces updates to their WhatsApp Group Video Call feature. Once you complete the steps, when you’re having problems with the taskbar, Start menu, or File Explorer, simply double click the batch file to reset the Explorer. Once you complete the steps, the enablement package will download and update any release of Windows 10 equal to or greater than version 2004 to version 21H2 as a regular cumulative update without reinstallation. Here you’ll find all collections you’ve created before. More information about IPP 3 can be found in OVIC’s Guidelines to the Information Privacy Principles. You need an active internet connection. Go to Menu, Download, and click to download the qBittorrent through VPN. Don’t like things coming up in the background. B appear only within 16 byte blocks,none span from one block to the next and are overlookedby this simple search. Apple Computer added the functionality to the Apple Macintosh with System 7’s Memory control panel in 1991, and kept the feature through the life of Mac OS 9. But I feel, we can still use WCF for many occasions. 3 pre 20170905 1 Beta Windows Execute Filemingw get setup. This sounds like what’s happening above — at least the latter scenario, that is. If you’d prefer being able to restart Windows Explorer more quickly and avoid using Task Manager altogether, you can put together a simple batch file to do the job. “ServiceDll”=”c:program files x86common filesakamai/netsession win e286960. Since owners of computers infected with spyware generally claim that they never authorized the installation, a prima facie reading would suggest that the promulgation of spyware would count as a criminal act. If you want to be able to run WGET from any directory inside the command terminal, you’ll need to learn about path variables in Windows to work out where to copy your new executable.
Camera Batteries and Chargers
We may earn a commission from affiliate links, at no additional cost to you. Html moved successfully. When your computer is getting full, BleachBit quickly frees disk space. Often, an app that shows a mistake message or crashes can be repaired with a basic solution: Just force it to close and reboot the app. You can use System File Checker Tool as follows. Some users and experts alike have reported that this program is considered bloatware or bundleware. Starting with iOS 11, there’s also an option to offload an app. You have the right to request deletion of your Personal Information at any time. NET Framework NGEN v4. Runtime Broker is a Windows process in Task Manager that helps manage permissions on your PC for apps from Windows Store. High keyThe opposite of “low key” meaning let everyone know. This second safe is the product of a merge conflit in iCloud sync. The Health and Medicine Division of the National Academies of Sciences, Engineering and Medicine have set Adequate Intake AIs for chromium. Spotify, are sent to this virtual device. Plus, you don’t have to hunt around for gaming partners thanks to these Battleship games you can play online, either alone or with others. There was a problem starting C:UsersdesktopAppDataLocalMicrosoftProtectprotecthost. Exe’s primary weakness is his overall childish nature when faced with failure or concepts he disagrees with. Source: Windows Central.
